Wondering how to create an incident response plan?
You’ve come to the right place.
Today, organizations witness a global increase in cyber-attacks that bring about confidential data leaks. According to a 2021 IBM report, the annual cost of a data breach rose from $3.86 billion to $4.24 million in 2021 alone. Likewise, cyber-attacks and data breaches impact the organization’s reputation and business operations.
So, why do you need an incident response plan if there are cybersecurity mechanisms to safeguard business operations?
You’re in luck. This post discusses the importance of incident response plans in helping to safeguard business operations against cyber attacks. We also dive into a step-by-step approach to help you create and execute your own incident response plan.
How to Develop an Incident Response Plan
There are several incident response phases.
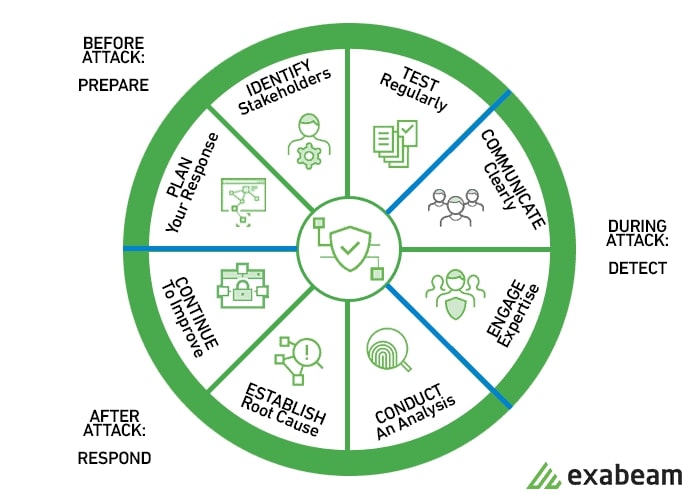
Credits: Exabeam.com
As per the National Institute of Standards and Technology (NIST) framework, there are four primary steps in developing an incident response plan:
Preparation
The preliminary phase begins with establishing the ground rules, training the incident response team, and identifying the appropriate tools and resources. This phase also emphasizes implementing a set of controls according to the risk assessment reports. During this phase, the organization works on building the capability to respond to any security incidents.
It also entails preventing them by ensuring high-level security for the systems, networks, and applications within the organization. To prepare for incidents, the organizations evaluate critical assets and identify which the ones that contain sensitive data. They also set up communication and coordination mechanisms for different scenarios. Here is a more detailed breakdown of the expectations set during the preparation phase:
- Keeping the contact information of the team members within the organization.
- Sharing that information with a select few outside parties where necessary, such as the law enforcement teams.
- Putting in place procedures to verify a contact’s identity, public encryption keys, and email addresses.
- Determining a secure messaging system to report incidents.
- Issuing tracking system to keep track of the incident status.
- Distributing smartphones for off-hour support and communication.
- Using software with encryption for contact with external agencies like a federal agency.
- Securing storage facilities to safeguarde sensitive materials and data.
- Maintaining a portable kit comprising critical materials necessary for evaluation and investigation.
Incident Prevention
This step within the preparation phase focuses on minimizing the occurrence of incidents.
It involves performing risk assessments of the systems and applications to understand various organizational threats. The incident response team solves the risk on a priority basis, considering the complexity and overall risk factor level.
Apart from that, the risk assessment teams must also implement standard configurations to tighten the hosts, including continuous monitoring of their configurations. Likewise, the incident response handlers work on securing the network perimeter and connection points and deploying malware prevention software to detect and prevent malware at the host, server, and application-client levels.
Moreover, organizations need to impart training to increase user awareness of standard policies and procedures for the correct uses of the network, systems, and applications and reduce the frequency of incidents.
Detection and Analysis
The second phase involves detection and analysis. When an incident occurs, the organization needs to determine the best course of action. This is when detection and analysis become essential. Security incidents arise from countless sources, so organizations must devise step-by-step instructions for resolving every incident using essential attack vectors and incident response strategies.
But the primary challenge for most organizations is accurate detection and assessment of potential incidents, such as their occurrence, type of incident, and the extent of the impact of the incident.
Accurate detection is more challenging because of different approaches to detecting incidents, such as manual approaches, antivirus-based detection, and automated detection mechanism. As such, while creating an incident response plan, it is essential to detect the incident based on two categories: precursors and indicators.
A precursor determines if an incident is likely to occur in the future, whereas an indicator helps identify any existing security incident. But it is essential to prioritize an incident according to the impact level and understand if any deviations are actual signs of a security breach.
Therefore, when a security incident occurs, an organization must have all the tools and technologies to collect and analyze the data based on the attack vectors that are common signs of a security breach. Besides, the teams need to be aware of the severity of the incident, document them, and notify the authorities in the event of a breach.
Containment, Eradication, and Recovery
Containment is vital to minimize the impact of a cybersecurity incident. Most incidents require containment, so the immediate goal of the teams is to prevent the incident from causing further damage. In such scenarios, the teams must collect as much evidence from all the computing resources to resolve the security incident. When you know who the attacking host is, the organization’s incident response plan must focus on identifying host addresses, gaining more information on the attack, and increasing monitoring of the communication channels of the attacking hosts.
After containing the incidents, the eradication procedure eliminates all the components of the incidents from the systems and applications of all the users. During the eradication, the teams work together to identify the root cause of the security breach. This includes the deletion of malware or removing any vulnerabilities from the network. Eradicating the threat involves consulting forensic data experts and working towards recovery by analyzing the breach information from the evidence.
However, the data recovery phase begins when the eradication is complete. These recovery phases comprise short-term measures for quick-fix or long-term recovery changes for the enterprise’s entire infrastructure. The recovery phase involves making several changes, from updating security measures to adopting best practices to address vulnerabilities and training employees to prevent similar breaches from occurring again.
Post-Incident Activity
The post-incident activity emphasizes learning from the incident. This includes learning and improving with training, discussions with different parties, and reflecting on how to deal with new threats with new technology integration. At the same time, during periodic meetings, team members discuss the learning of previous cyber threat encounters. But it is necessary to conduct these meetings no later than two weeks from the recovery to ensure accurate information is available for analysis and discussion. Organizations devising an incident response plan must conduct these meetings with themes revolving around critical questions that include:
- Understanding which incident took place and at what times?
- How effective were the incident team members in dealing with the incident, and if proper records about these incidents are available?
- What information helps deal with the incident as quickly as possible?
- What are the steps and actions taken during recovery?
- What are the different approaches that the management needs to take next time if any similar incident occurs?
- Has information sharing improved?
- What are the additional tools required to detect and analyze future incidents?
Common Security Incidents
There is a wide range of common cyber incidents that every organization considers alarming:
- Different types of malware and ransomware
- Social engineering
- Data breaches and data leaks
- Email spoofing
- Denial of service
- Brute force attacks
- OWASP application vulnerabilities
- External media
- SQL injections
- Cross-site scripting
- Man-in-the-Middle attacks
Incident Response Plan: Roles and Responsibilities
A cyber incident response plan must provide incident response roles for post-incident analysis. In such scenarios, the disaster recovery plan must avoid duplicate work to help speed up identifying affected parties. Resolving incidents become more complex when there is a lack of communication, coordination, and well-laid responsibilities. As a result, several tasks become repetitive, leading to a longer recovery time. That’s why effective security practices require clear organizational roles and responsibilities. Most incident response team members comprise experts such as:
Incident Manager
The incident manager assumes the primary role of the incident response teams. They are responsible for directing all the efforts and resources toward solving the security incident. Incident response manager delegates and assigns different roles and responsibilities to team members according to the nature of the incident and reports all progress to the top-tier management.
Senior Tech Lead
Tech leads are senior technical professionals investigating the security event’s root cause. They identify the problem areas that need attention and understand the nature of the breach to devise an immediate action. Likewise, tech leads communicate the action plan to other team members and report the updates to the incident manager.
Communication Manager
As the name suggests, the communication manager’s sole responsibility is to manage communication among the incident response team members. These professionals also communicate the incident to customers, the public, legal and federal authorities, and other stakeholders in the organization.
Legal Representative
An incident response plan also needs the appointment of a legal team to perform a thorough investigation of the cybersecurity incidents and offer guidance for compliance and other standard security protocols by law enforcement authorities.
Analysts
These analysts are the primary researchers within the organization who perform tasks like collecting evidence and other records in the context of the incident for thorough security analysis. In addition, they implement various security tools to perform threat intelligence to determine incident definitions and employ various analytical measures to identify the primary cause of the incident, provide the reports to the incident manager for further investigation, and employ better threat detection mechanisms and containment strategy.
Incident Response Plan: Key Takeaways
An incident response plan must have some vital elements to be more effective for an organization.
The incident response plan must include actionable and applicable steps but allow significant flexibility to tackle a wide range of incidents or new cyber threats.
Maintain a precise communication mechanism that details the hierarchical chain of whom to communicate in the event of an incident.
But above all, having support from senior management to transform the organization’s environment goes a long way in improving information flow within the organization for effective handling of incidents.